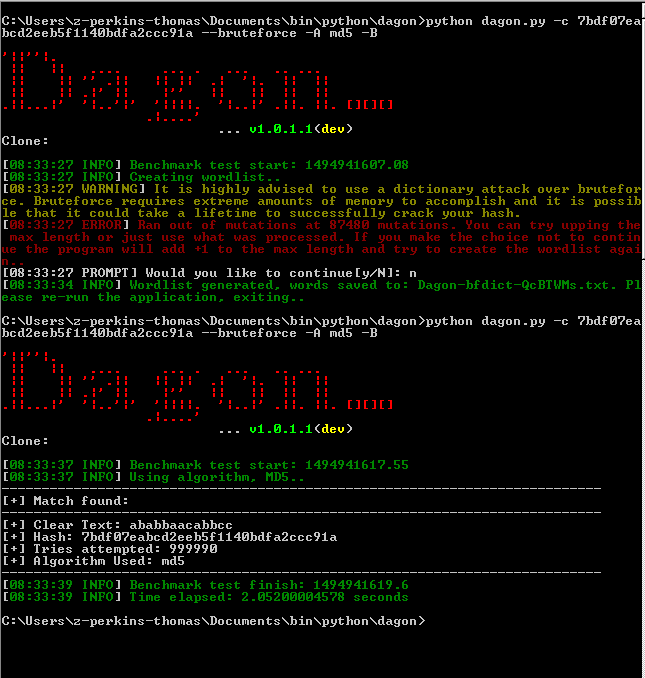
Brute-force stream routes; Brute-force credentials; Make screenshots on accessible streams; Generate user-friendly report of the results:.txt file with each found stream on new line.html file with screenshot of each found stream; Report files. Result.txt: Each target is on a new line. Import to VLC: change extension to.m3u and open in VLC. Hello guys, Today we will be learn How to create MD5 brute force script using Python. What is brute-force Attack? Brute-force attack also known exhaustive key search; Process of checking all possible keys; Using a dictionary to attack with; Dictionary is usually more effective than searching the whole key space. Exponentially grow with. Brute forcing a binary file input with Python. Later on, I was told that a brute-force approach could have worked as well, since the string length was not prohibitive. Indeed, in the worst scenario and with the most naive technique, I would have had to try out inputs (with 136 being the string length). Not small, but not prohibitive.
- Python Md5 Brute Force Tutorial
- Brute Force Attack
- Brute Force Download
- Python Md5 Brute Force Example
- Python Md5 Brute Force Example
- Python Md5 Brute Force Programming
This article has been on my disk for a long time ~ 16 year 9 Of the month . this Python I haven't made much progress . Now all 17.4 了
Ah ~~
Python And POST Submit decryption MD5
Write it in easy language md5 I don't feel any sense of accomplishment after decrypting the software . use Python It's so much better to realize , Although it's simple , Otherwise, I wouldn't have .
Obvious , To decrypt MD5 The first problem to solve is to submit md5. It's about contact Python Of post 了 .
【 First , Grab the bag . Sacrifice the magic -firebug】

We turn on firebug, Open our md5 Decrypt website , And then just type in any md5 To decrypt , Get the form he uploaded , We cut it off and change it . This is what I cut off :
__VIEWSTATE /wEPDwUKMTM4NTE3OTkzOQ9kFgJmD2QWAgIFDxYEHgVjbGFzcwULdGlwIHN1Y2Nlc3MeCWlubmVyaHRtbAWRATxpIGNsYXNzPSJpY29uZm9udCI+JiN4ZTY5MTs8L2k+PHAgY2xhc3M9ImluZm8iPuaCqOafpeivoueahOWtl+espuS4suaYr+KAnDxlbT5hYzU5MDc1Yjk2NGIwNzE1PC9lbT7igJ0s6Kej5a+G55qE57uT5p6c5Li64oCcPGVtPjEyMzwvZW0+4oCdITwvcD5kZPIZDYK0nljm9jNu3+z+aROsKjit
__VIEWSTATEGENERATOR CA0B0334
__EVENTVALIDATION /wEWAwLkuLOgDALigPTXCQKU9f3vAm7mreoHjgJqcpJYT7YZ4aInh4XU
key ac59075b964b0715
jiemi MD5 Decrypt
After the arrangement :
'__VIEWSTATE':'/wEPDwUKMTM4NTE3OTkzOQ9kFgJmD2QWAgIFDxYEHgVjbGFzcwULdGlwIHN1Y2Nlc3MeCWlubmVyaHRtbAWRATxpIGNsYXNzPSJpY29uZm9udCI+JiN4ZTY5MTs8L2k+PHAgY2xhc3M9ImluZm8iPuaCqOafpeivoueahOWtl+espuS4suaYr+KAnDxlbT5hYzU5MDc1Yjk2NGIwNzE1PC9lbT7igJ0s6Kej5a+G55qE57uT5p6c5Li64oCcPGVtPjEyMzwvZW0+4oCdITwvcD5kZPIZDYK0nljm9jNu3+z+aROsKjit',

'__VIEWSTATEGENERATOR':'CA0B0334',
Python Md5 Brute Force Tutorial
'__EVENTVALIDATION':'/wEWAwLkuLOgDALigPTXCQKU9f3vAm7mreoHjgJqcpJYT7YZ4aInh4XU',
'key':md5,
'jiemi':'MD5 Decrypt '
It's not hard to see that there are five parameters , But what works is ‘key’ This parameter . We just need to change it to get the effect we want .
【 And then we build a data To send 】
data={
'__VIEWSTATE':'/wEPDwUKMTM4NTE3OTkzOQ9kFgJmD2QWAgIFDxYEHgVjbGFzcwULdGlwIHN1Y2Nlc3MeCWlubmVyaHRtbAWRATxpIGNsYXNzPSJpY29uZm9udCI+JiN4ZTY5MTs8L2k+PHAgY2xhc3M9ImluZm8iPuaCqOafpeivoueahOWtl+espuS4suaYr+KAnDxlbT5hYzU5MDc1Yjk2NGIwNzE1PC9lbT7igJ0s6Kej5a+G55qE57uT5p6c5Li64oCcPGVtPjEyMzwvZW0+4oCdITwvcD5kZPIZDYK0nljm9jNu3+z+aROsKjit',
'__VIEWSTATEGENERATOR':'CA0B0334',
'__EVENTVALIDATION':'/wEWAwLkuLOgDALigPTXCQKU9f3vAm7mreoHjgJqcpJYT7YZ4aInh4XU',
'key':md5,
Maverick dmg download. 'jiemi':'MD5 Decrypt '
}
【 Use the last lesson requests In the command post】
a=requests.post(b,data=data) # Hair data To URL(b)
【 I want what we want 】
text1=re.findall(' The result of decryption is “<em>(.*?)</em>',text) # stay text Take the corresponding content in text1 in
【 And then print one by one ( Obviously we can only have one )】
Because we don't study regularity , The return value of this command should be like E Regular in . Take all ! The return value of that is an array , stay Python It's called in Chinese list. We still need to take them out one by one .
【 Add one input And then enjoy the quick md5 Decrypt the experience ! I test that it's OK to have spaces , It should be different from site to site .】
Python md5 More related articles decrypted
- Share some free MD5 Decrypt website
I downloaded a few recently mdb file , Tens of thousands of them md5 And thousands of sha512( Actually still have stationmaster to use 512 Put it directly in the library , Nima takes up more space ), I use C# I wrote a tool storm A small part of the force , Probably not 3% Well , It took me two days , The computer is jammed , effect ..
- free MD5 Decrypt website , Easy to crack md5 password ,mysql5/mysql323,ntlm,salt password
md5 Decrypt website :http://cmd5.la Website language :php Free Index :*** (8 The lower case numbers and letters in the digits are free ,11 In place numbers are free ) Decryption scope :***** ( covers 1-12 A lot of common passwords and special ..
- md5 Decrypt the conjecture
md5 Decrypt the conjecture One . summary One sentence summary : It can be used skillfully ( Commonly used password , Related information ) The brute force of . Two .md5 Decrypt the conjecture 1. Brute force Actually md5 It's also made up of those common string groups 32 A cipher , So you can put those common strings ( ..
- About MD5 Decrypt website .www.cmd5.com
I heard about this website for the first time , My name can be decrypted , And still need to pay for clear text ! As we all know ,md5 Encryption is our usual way of encryption , The advantage of this encryption is that it's irreversible . And the ciphertext calculated in any environment should be the same , So we're going to board ..
- python md5 Encrypt Chinese
import md5 md5.new(u' chinese ').hexdigest() Will fail , The report ascii The code can't be decoded 0x.. as a result of md5 Will automatically convert encrypted data into bytecode , If there is no detailed coding , It may be that ..
- python Encryption and decryption
1. Use base64 s1 = base64.encodestring('hello world') s2 = base64.decodestring(s1) print s1, s2 result 1 2 .. Bluestacks download for mac big sur.
- python Encryption and decryption (base64, AES)
1. Use base64 s1 = base64.encodestring('hello world') s2 = base64.decodestring(s1) print s1, s2 result 1 2 ..
- Python md5 sha1 Use
edition : Python 2.7 explain : Python Built in hashlib There is md5 and sha1 Encryption method , You can use it directly . md5 encryption import hashlib data = 'This ..
- Python MD5 The algorithm uses
## md5 Introduction to the algorithm 1. ** brief introduction ** MD5 Message digest algorithm (MD5 Message-Digest Algorithm), A widely used cryptographic hash function , I can produce one 128 position (16 byte ) Hash value ..
Random recommendation
Brute Force Attack
- Red rice 2A High configuration brush machine record
2014816 Model : Red rice 2A High configuration version Model of equipment :2014816 CPU: qualcomm Wire brush :fastboot platform http://192.168.7.118/MesReports/Reports/Cutting ..
- flash2x、flax
http://flax.so/ Cattle from LeetCode Online Judge
- Python Data processing ---- Processing of fixed length data
scene : Sometimes we process a lot of data , High performance requirements , And the data are fixed length , For example, the mobile information registration form is processed : name ID card information Phone number These are fixed length , Today, Xiaohua will teach you how to process this kind of data . Mojave on unsupported mac. Step one : ..
- Time format conversion String2datestyle
Time format into string Tool class : package cn.javass.util; import java.text.DateFormat; import java.text.SimpleDateFo ..
- html5 canvas The color of the picture is reversed
<!doctype html> <html> <head> <meta charset='utf-8'> <title> ..
- In the oracle When inserting data , How to deal with it excel Read time null value
// If from excel When the time value read in is null , Do the following transformation string YDKGSJ = string.Empty; if (dbdata.Rows[i][' Set the start time '].ToSt ..
- first Python Program - Email Manager Demo
I saw some basic Python After the novice tutorial , I feel deeply that Python Simple and powerful , This is my first Python Demo. Here is the complete code and execution screenshot . Code : # encoding: utf-8 '' ..
- [Leetcode][Python]48: Rotate Image
# -*- coding: utf8 -*-''__author__ = 'dabay.wang@gmail.com' 48: Rotate Imagehttps://leetcode.com/pr ..
- Python Building tools buildout Introduction and use of
I came to work in a new company , The first is to build up your own environment . Zhihu used it buildout As python Project building tools . So what is buildout ? buildout It's an automated build tool . from Zope Team opening ..
- A passbook 1633【 example 3】Sumdiv
1633:[ example 3]Sumdiv The time limit : 1000 ms Memory limit : 524288 KB [ Title Description ] The original question comes from :Romania OI 2002 seek ABAB Sum of all divisors of mo ..

Brute Force Download
Python Md5 Brute Force Example
I use python 2.7, and I have a simple multitheaded md5 dict brute: # -*- coding: utf-8 -*- import md5 import Queue import threading import traceback md5_queue = Queue. Python Parallel hash bruteforce. @Blender This is just a learning exercise and python is the language I understand the. Parallelize brute force generation. How to write a brute-force password cracker. The algorithm is md5(concat(md5(password), salt)). Here is my code written in python. This module implements a common interface to many different secure hash and message digest algorithms. Included are the FIPS secure hash algorithms SHA1, SHA224.
Note Feeding string objects into update() is not supported, as hashes work on bytes, not on characters. Constructors for hash algorithms that are always present in this module are sha1(), sha224(), sha256(), sha384(), sha512(), and. Md5() is normally available as well, though it may be missing if you are using a rare “FIPS compliant” build of Python.
Python Md5 Brute Force Example
Additional algorithms may also be available depending upon the OpenSSL library that Python uses on your platform. Program De Verificare Plagiat Gratuit. On most platforms the sha3_224(), sha3_256(), sha3_384(), sha3_512(), shake_128(), shake_256() are also available.
Sha224 ( b 'Nobody inspects the spammish repetition' ). Hexdigest () 'a4337bc45a8fc544c03f52dc550cd6e1e87021bc896588bd79e901e2' hashlib. New ( name [, data ] ) Is a generic constructor that takes the string name of the desired algorithm as its first parameter. It also exists to allow access to the above listed hashes as well as any other algorithms that your OpenSSL library may offer. Fast And Furious 5 Rio Game here. The named constructors are much faster than and should be preferred. Using with an algorithm provided by OpenSSL. Changed in version 3.1: The Python GIL is released to allow other threads to run while hash updates on data larger than 2047 bytes is taking place when using hash algorithms supplied by OpenSSL.
Digest ( ) Return the digest of the data passed to the method so far. This is a bytes object of size which may contain bytes in the whole range from 0 to 255. Securecrt 7.0.3 Portable Win X86 more. Hexdigest ( ) Like except the digest is returned as a string object of double length, containing only hexadecimal digits. This may be used to exchange the value safely in email or other non-binary environments.
Copy ( ) Return a copy (“clone”) of the hash object. This can be used to efficiently compute the digests of data sharing a common initial substring. SHAKE variable length digests The shake_128() and shake_256() algorithms provide variable length digests with length_in_bits//2 up to 128 or 256 bits of security. As such, their digest methods require a length. Maximum length is not limited by the SHAKE algorithm.
Python Md5 Brute Force Programming
Digest ( length ) Return the digest of the data passed to the update() method so far. This is a bytes object of size length which may contain bytes in the whole range from 0 to 255. Hexdigest ( length ) Like except the digest is returned as a string object of double length, containing only hexadecimal digits. This may be used to exchange the value safely in email or other non-binary environments.